
NORDSON Telecommunications Security Management
<> Computer Room Access Control Management
<> Personnel Tracking
<> Personnel Time Attendance
<> VIdeo Monitoring and Real-time Photos
<> Alarm Output and Fire Control Controller
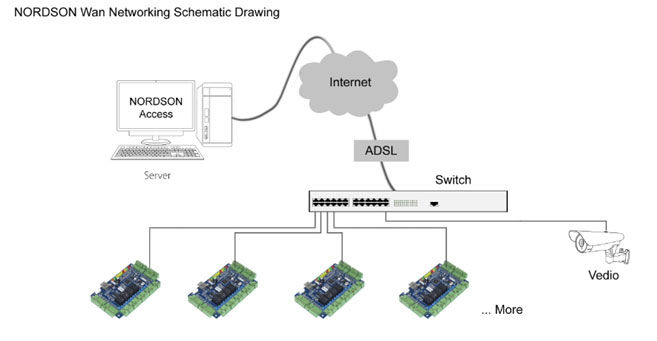
<> Computer Room Access Control Management
The establishment of security zone can prevent unauthorized access to Hospital and realize closed management. Day students and residential students can be assigned into different access groups. Once exceptional access of residential students is found, alarm will be sent to guard. Nobody can access the security zone with other person’s card.
> Each access controller can hold 20,000 users, for example, single door controller can manage 20,000 users; for two-door controller, if door #1 manage 5,000 users, then door #2 can manage at most 15,000 cards, so as to the four-door contoller.
> 100,000 event buffers can be stored offline. Every event buffer includes informations such as card #, time, address, getting across or not etc. If the storage space overloaded, old information will be deleted automatically so to save space for new records. Your option to activate whether to record button unlocking and alarm information, if unactivated, button unlocking and alarm information will not be recorded.
<> PersonnelTracking
Access Control System can track student’s activities such as the time of entering or leaving school. Access Control System can conveniently check such attendance status as late to school, absenteeism and leave early etc., which helps to supervise personnelstatus and realize scientific managament.
> Real time monitor each card swiping,. Can display the card holder ' s photo which was prestored in the software, so the security guard can check if the card holder is the one intended to unlock the door. If magnete lines are connected, you can check which door is open or close. Valid cards swiping records will be marked in green; invalid card swiping records will be in orange and alarm records will be in red so to call the security guard ' s attention. If video monitor device installed, it can record the real time video and photo when you swipe the card.
<> Personnel Time Attendance
personnelattendance can record when the students enter or leave the school. This helps teachers to supervise the availability of students.With its powerful alarm function, Access Control System can interwork with fire system. Once an event occurs, Access Control System can quickly open the door and create on-site alarm to help students escaping from dangerous zone.
Flexible time setting
> Can define holiday period
> Can specify a certain door to do time and attendance
> Can set the number of daily card swiping
> Flexible Sat time and attendance setting
> Can import leave application form, flexibly add and customize the holiday name
> Detail time and attendance summary report
> Can customize the report form
> Can set that certain person excluded from time attendance list
<> VIdeo Monitoring and Real-time Photos
If video equipment connected, it can capture your photos and 3 seconds vedio record when you swip the card or turn on the button. It ' s convenient for the administrator to check if the card holder is the one owns the card. And afterwards you can check the records. But this function requires both the computer and software vedio supervision interface are in operation.
<> Alarm Output and Fire Control Controller
Access Control System can interwork with fire system. Once an event occurs, Access Control System can quickly open the door and create on-site alarm to help students escaping from dangerous zone.
> Connect with the infrared sense probe, sense organ or door magnet, if someone break in illegally, the infrared sense organ will start the alarm system.
> Need to connect with the gas sense organ, smoke sense organ etc.
Connect with the emergency button, if robbery happen inside the room, people can push the emergency button and alarm will be started.Flexible Sat time and attendance setting












 Add: Room 417, Sun\'gang Building, No. 23, Baogang
Add: Room 417, Sun\'gang Building, No. 23, Baogang Tel: +86-755-8637 7711
Tel: +86-755-8637 7711  Fax: +86-755-8276 2979
Fax: +86-755-8276 2979  Website:
Website: 





